Security Analytics. Delivered
Cybersecurity that prevents threats at faster speed, greater scale, and higher accuracy than humanly possible
Key Strengths

Unified Platform
Single, unified platform for:
- Online monitoring
- Log Management
- Threat Hunting
- Compliance
- Metrics and analytics
- Incident Response

Cloud Native Architecture
Modern cloud native architecture
Designed for cloud 3 Vs:
- Volume
- Velocity
- Variety
SaaS model delivers operational efficiency

Powerful and Flexible Analytics
Best of breed analytics
Flexibility without complexity
- Custom use cases with advanced analytics directly on the UI
Advanced users can also “bring your own analytics”

Top-notch Content
- Quick Time to Value
- Extensive Threat and Technology coverage
- Simplified testing and deployment
- Premium apps for vertical oriented content
The Elements of the Platform

Securonix Next-Gen SIEM
Cloud-based SIEM platform.

Securonix UEBA
Detect unknown threats.

Securonix SOAR
Facilitates rapid, playbook-driven incident response.

Securonix NTA
Network traffic analysis expands threat visibility.

Securonix Security Data Lake
Unlimited scalability.

Cloud Connector
Collect data from and monitor multi-cloud infrastructure and applications.

App Connector
Ingest data directly from enterprise and custom applications.

Securonix API
Easily integrate legacy or new applications not previously supported.
CUSTOMER TESTIMONIALS
The Splunk Use Case Model from Positka is a game changer. All Splunk users need to look into.
~ CISO,
Major Telco
The speed with which Splunk Use Cases were implemented by Positka ihelped us deliver to our customer requirements in record time.
~ CTO,
High Tech SaaS provider
Positka helped us with amazing insights by focusing on the data science with some of the best data scientist we have worked with.
~ Director of Analytics,
Global Technology Player
Highlights
Accessibility
- Hosted on Public Cloud, accessible from anywhere, any device, no VPN required
- Supports Cloud based SSO – SAML, OAuth
Architecture
- Multi-tenant architecture, logical segregation of data
- Dedicated application per customer
- Full App GUI access
Security
- SOC2 Type 2 certified
- Encrypted secure channel
- On-prem to cloud data transfer restricted to single IP address
Operations
- SNYPR-EYE enables configuration and monitoring of infrastructure and application components
- Alerts on health of system, import jobs, behavior jobs, EPS, etc.
Cloud & On-prem feeds
- Cloud to cloud integrations via API
- On-prem data feed imports via RIN
- Identity/HR, Threat Intel other context data correlation
Securonix Managed
- Access to the latest software version and patches
- Latest threat models and use case
- Best-in-class SME support 24×7 operations and management
Securonix Next Gen SIEM Solution
- Gain Profound Visibility and Scalability
- Decrease Mean Time To Detect Threats
- Decrease Mean Time To Respond to Threats
- Realize faster return on investments
- Leverage Securonix cloud-native next-generation SIEM with multi-tenancy, offering complete visibility into on-premises, cloud, and edge devices, and scale easily as your data requirements grow.
- Cloud-Native Infrastructure for Multi-Tenancy: Full next-generation SIEM capabilities located wholly in the cloud, without infrastructure to manage, and with unlimited scalability.
- Built-In Cloud Application Integrations: Securonix ingests data from cloud applications and infrastructure, as well as from on-premises solutions, giving you visibility across your hybrid infrastructure. Benefit from real-time enrichment with over 350 cloud connectors built in.
- Focus your security team on addressing real threats instead of chasing false alarms. Securonix removes false positives and spots advanced threats, giving your team visibility into threats such as privileged account abuse and other hard to detect use cases that require behavior analytics.
- User and Entity Behavior Analytics: Our advanced analytics learns what normal behavior patterns are and creates baselines in order to identify outliers. Gain out-of-the-box use cases, delivered in the form of threat models and built-in connectors, that enable rapid deployment and quick time to value.
- Threat Chain Workflow: Enables attack identification by linking together a chain of related events, sequenced logically to enable faster detection of threats such as privileged account abuse, IP theft by departing employees, and other types of data exfiltration.
- Disparate, disconnected security solutions slow down a security analyst’s ability to detect and respond to threats.
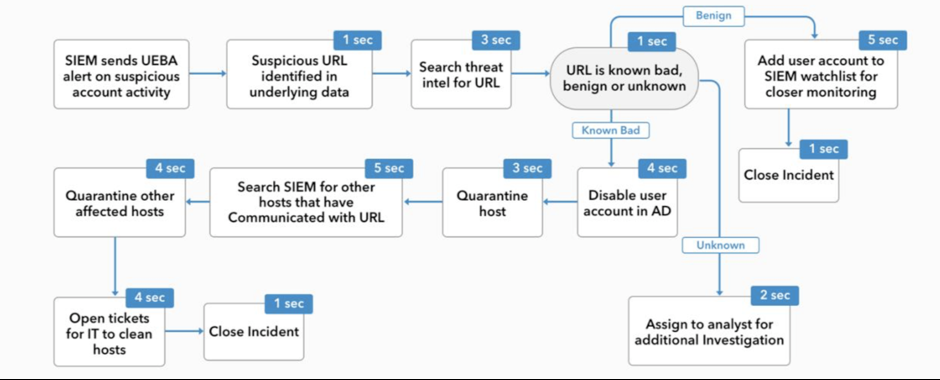
- With intuitive analyst workflow for threat hunting and incident response, Securonix SOAR drives down response times.
- Spotter Search: The Spotter search capability gives threat hunters the ability to search across recent and historical data without impacting SIEM performance.
- Response Bot: Take advantage of automation and playbooks that help Tier 1 analysts to act like Tier 3 analysts, driving down response times.
- Case Management: Built-in case management capabilities efficiently track and report on the incident response process.
- Leverage the only cloud-native next-generation SIEM with multi-tenancy where all solutions – SIEM, UEBA, SOAR, and NDR – are part of one platform.
- One Seamless Platform for SIEM, UEBA, SOAR, and NDR in the Cloud: Instead of disparate solutions for UEBA, SIEM, NDR, and SOAR, experience quantifiable ROI from the efficiency of using a single-pane-of-glass solution.
User and Entity Behavior Analytics (UEBA)
- Accurately Detect Advanced Threats
- Quick Time To Value and Rapid Deployment
- Shorten Time To Respond With Automated Security
- Protection in the Cloud, for the Cloud
- Securonix UEBA detects unknown, zero day, and advanced persistent threats using pre-built threat content focused on insider threats, fraud, and other key use cases.
- Entity Context: The solution generates comprehensive identity and risk profiles for every user and entity in your environment.
- Advanced Behavior Analytics With Machine Learning: Out-of-the-box analytics, along with patented machine learning algorithms (both supervised and unsupervised) help identify multi-level threats that span multiple alerts/events, enabling you to find complex threats with minimal noise.
- Out-of-the-box use cases, delivered in the form of threat models and built-in connectors, enable rapid deployment and quick time to value.
- Pre-Built Use Cases: Benefit from immediate, one-click access to content for insider threat, cyber threat, fraud, cloud security, and business applications use cases.
- Faster Search: Leveraging cloud-based, big data storage and search technology, Securonix delivers faster search results and quicker threat hunting capabilities. Search in real time on streaming data, as well as on long-term data
- Built-in incident playbooks include configurable automated remediation actions to shorten time to respond.
- Automated/Semi-Automated SOAR Capabilities: With built-in incident playbooks, custom playbooks, and response identification
- Includes Response Bot: An artificial intelligence-based recommendation engine that suggests remediation actions based on the previous behavior patterns of Tier 3 analysts.
- A cloud-native solution with unlimited scale, that can grow with you. Integrates with your cloud data natively with 350+ out-of-the-box cloud connectors.
- Cloud and Application Analytics: Detect threats to your cloud and enterprise applications, such as data exfiltration from online file sharing applications or unauthorized instance creation on web infrastructure services.
- Support for Data Privacy and Compliance: Enforce role-based access control (RBAC), data masking, and other privacy controls in compliance with GDPR and other industry requirements. Securonix provides broad support for key industry standards such as GDPR, CCPA, SWIFT, and NIST.
Security Orchestration Automation and Response (SOAR)
- Prioritize Threats Using a Centralized Solution
- Intelligent, Automated Incident Response
- Track & Improve Incident Response
- Leverage a big data architecture with built-in machine learning to prioritize high-risk threats.
- Single Source of Truth: Stop switching across disparate tools. With Securonix SOAR you have a single-pane-of-glass, integrated view across your entire security environment, allowing your security operations center (SOC) to quickly identify and respond to incidents.
- Integrations with Over 275 Connectors: CISOs need security tools that integrate with their entire tech stack in order to provide the best ROI and save their team time when responding to incidents. Securonix SOAR works seamlessly with our SIEM and UEBA solutions
- Automated response increases the productivity and efficiency of your SOC team, instead of relying on time-consuming manual investigation.
- Built-In Playbook Actions: Securonix SOAR provides automated incident orchestration and response with 275+ connectors and 3000+ playbook actions. Securonix playbooks are provided out of the box and are fully customizable.
- Machine Learning: Securonix SOAR uses machine learning to learn from senior analysts so that it can make recommendations on next steps to take during incident response and even automate future response actions.
- Manage your alerts, respond to threats faster, and increase security analyst morale, all while realizing cost savings.
- Case Management: Case management can be used to show investigation steps for a compliance audit, data breach, or for internal training.
- Incident Response Reporting: Securonix SOAR provides a measurable ROI and metrics on resolved incidents, mean dwell time, mean time to respond, playbooks and action run, as well as time and cost savings.
Securonix SOAR Benefits
Maximizes cost savings through integration, automation and higher efficiency
Solution Benefits
✔Faster Investigations / Measurable ROI
-
- SIEM with UEBA and SOAR automation results in less operational overhead in training and enablement
- Measure and boost SOC efficiency with SLA tracking
✔Prioritized Threats / Improved Efficiency
-
- High fidelity alerts allow a SOC to scale with fewer analysts
✔Rapid Time to Value (TTV)
-
- Large number of OOTB connectors and integrations allows new use cases to be rapidly implemented

Challenges Addressed
![]() Alert Fatigue
Alert Fatigue
Average time before T1 analysts quit their jobs due to it’s repetitive nature
![]() Slow Response Time
Slow Response Time
Organizations receiving 500+ critical alerts investigate only 11 to 25 alerts/day
![]() Increased Risk / Exposure
Increased Risk / Exposure
An adversary is able to survive in the enterprise due to missed alerts
![]() Lack of skilled professionals
Lack of skilled professionals
Predicted shortage of cybersecurity professionals by 2019
Delivering SOC Efficiencies with Security Orchestration Automation and Response (SOAR)
General Dynamics Whitepaper, Jun 2018
Migrating existing SIEM to Securonix Cloud

Case Study - India’s largest Cyber Fusion Center
Key Value Adds
- Security Analytics on 3 Lakh EPS
- Key Machine Learning Use cases
- Cyber Fraud
- Insider Risk
- Financial Fraud
- Application Analytics
- Custom Machine Learning models
- Dedicated tenant in India cloud
- Private Cloud for the Bank
- BYOK based encryption
- RBI approved
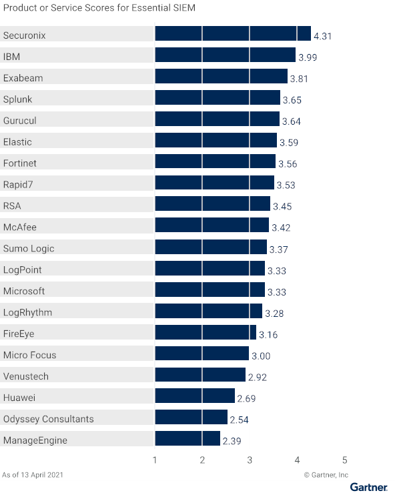
Competitive advantages over Splunk and IBM
- Richness of Machine learning
- Splunk does not have pre-built content – heavy on services
- Address risk beyond Cyber fraud
- SWIFT fraud
- ATM fraud
- Quickest Time to Value
- Set up the infra for 3 Lakh EPS in less than 2 weeks
- Almost at full capacity in less than 6 months
- Value
- Threats beyond current Q-Radar in 2 months
- Integrated cloud landing zones