IBM Security Portfolio
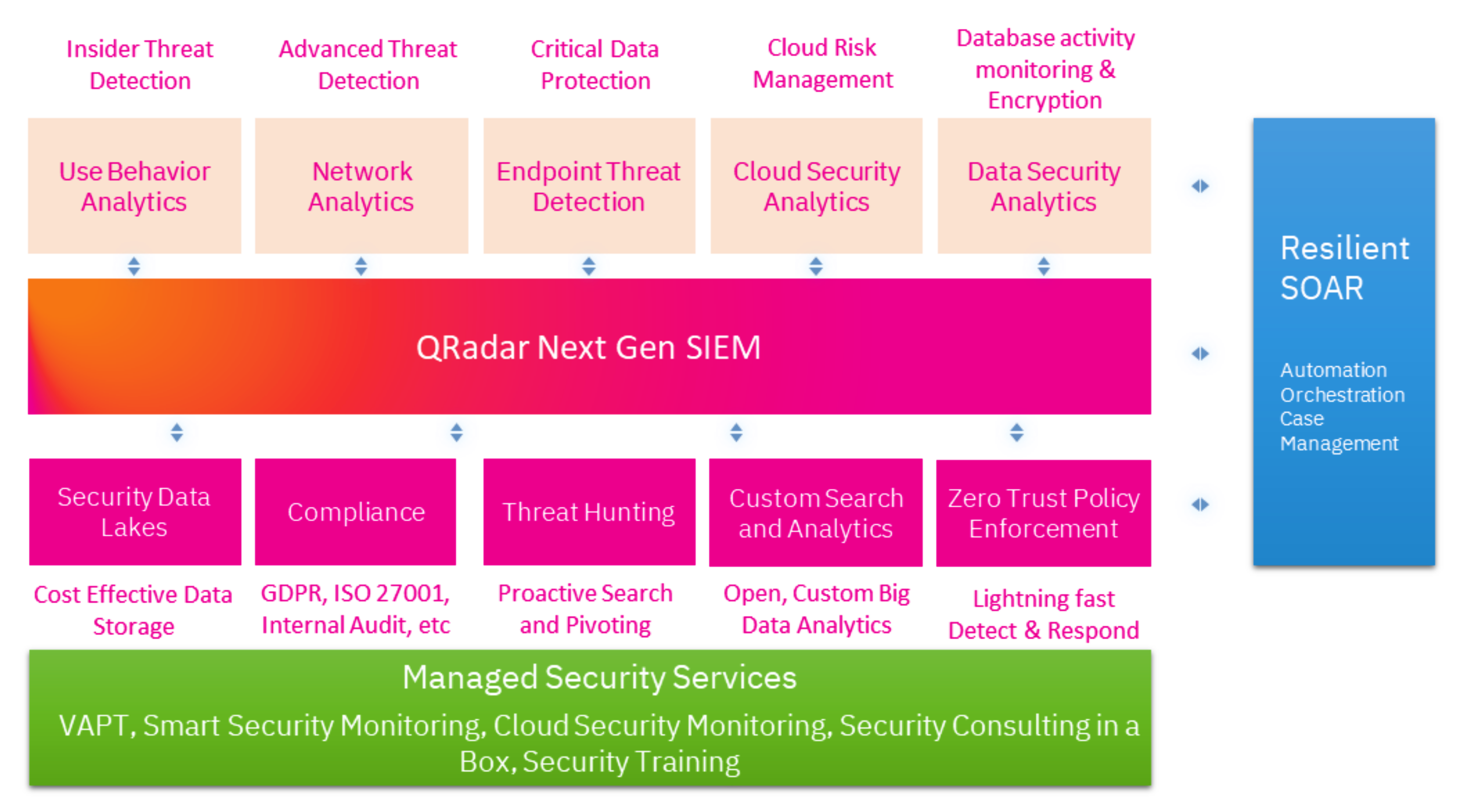
QRadar SIEM
Centralized visibility to detect, investigate and respond to your most critical organization-wide cybersecurity threats, comes bundled with UBA and Network Insights
Guardium DAM
Take a smarter, more adaptive approach to protect critical data. Discover where your data is most at risk, gain contextual insights and analytics, and take action to monitor, protect and mitigate issues.
Cloud Pak For Security
An open multi-cloud platform to gain all security insights at one place, take action faster, and modernize your security architecture
Resilient (SOAR)
Accelerate incident response with automation, process standardization and integration with your existing security tools
Identity & Access Management
Put zero trust into action to secure and empower your workforce by securely connecting every user with the right level of access
Guardium Data Encryption
Prevent unauthorized data access , deploy granular data encryption at the file, database, or application level and protect data from compromise
Complete Security Coverage – Powered by IBM Security
Talk to us on how IBM can strengthen your security posture

Positka's Professional Services Offerings
Growing need for a reliable partner to help to secure the evolving enterprise
At Positka we offer, end-to-end services starting from designing the suitable security architecture, deploying solutions in your environment as per the designed architecture, migration of standalone to distributed or clustered environment, supporting the maintenance of the deployed platform and Optimization for high availability and better performance.
Align
We help clients align security to their business
- Baseline security posture & maturity gap assessment
- Policy to framework mapping (MITRE, NIST,ISO)
- Cloud Security & Monitoring Strategy
- Security compliance assessment for industry standards (for ex PCI DSS. HIPAA, SOX)
Protect
We help clients protect digital users, assets, and data
- Architecture design and Greenfield implementation
- Custom DSM for unsupported data sources
- Appliance deployment per recommended configuration
- Configure components, HA & Rule activation
- Integrate Cloud end-points, APIs and connectors
Manage
We help clients manage their defence against growing threats
- On-board new data sources and Building Blocks
- Upgrade the architecture and appliance firmware
- Reduce noise and false positives in alerts
- Address loss of events
- Technical support & Performance optimization
Modernize
We help clients modernize security applications and be future ready
- Version upgrade
- Refresh/Retune contents
- Design Connectors & Contents for Cloud
- Design new architecture for upcoming environment
Access to IBM certified consultants and blend of domain expertise in Security, IT Operations, Artificial Intelligence / Machine Learning
OUR CLIENTS

LARGEST FAST FOOD RETAILER

LARGEST MARKETPLACE

LEADING RIDE-HAILING APP

TOP GLOBAL BANK
TALK TO AN EXPERT ON HOW IBM CAN HELP YOU
CUSTOMER TESTIMONIALS
The IBM Qradar Use Case Model from Positka is a game changer. All IBM Qradar users need to look into it.
~ CISO, Major Telco
The IBM Qradar Use Case Model from Positka is a game changer. All IBM Qradar users need to look into it.
Speed with which IBM Qradar use cases were implemented by Positka, helped us deliver to our customer requirements in record time.
~ CTO, High Tech SaaS provider
Speed with which IBM Qradar use cases were implemented by Positka, helped us deliver to our customer requirements in record time.
Positka helped us with some amazing insights by focusing on the data science with some of the best data scientists we have worked with.
~ Director of Analytics, Global Technology Player
Positka helped us with some amazing insights by focusing on the data science with some of the best data scientists we have worked with.
GET IN TOUCH
Whether you are looking for general information or have a specific question, we want to help. Fill the form below or drop us a line at susan@positka.com.